Microsoft Security Tools and Guidance
 Advanced Persistent threats are a hot security topic lately. According to Wikipedia, APT usually refers to a group, with both the capability and the intent to persistently and effectively target a specific entity. The term is commonly used to refer to cyber threats, in particular that of Internet-enabled espionage using a variety of intelligence gathering techniques to access sensitive information.
Advanced Persistent threats are a hot security topic lately. According to Wikipedia, APT usually refers to a group, with both the capability and the intent to persistently and effectively target a specific entity. The term is commonly used to refer to cyber threats, in particular that of Internet-enabled espionage using a variety of intelligence gathering techniques to access sensitive information.A modern attack performed by APT is the “Pass the Hash”. According to a whitepaper from Microsoft, while performing a PtH attack, an attacker obtains elevated read/write permission to privileged areas of volatile memory and file systems, which are normally only accessible by system-level processes on at least one computer. Second, the attacker attempts to increase access to other computers on the network by:
- Stealing one or more authentication credentials (user name and password or password hash belonging to other accounts) from the compromised computer.
- Reusing the stolen credentials to access other computer systems and services.
This sequence is often repeated multiple times during an actual attack to progressively increase the level of access that an attacker has to an environment.
Regarding free assessment tools from Microsoft, as well as protection software, there’s a really nice compilation on the “Irish IT Professional” technet blog. You get to know tools like Microsoft Security Compliance Manager, Microsoft Baseline Security Analyzer and Microsoft Security Assessment Tool.
Regarding security tools for footprinting, internal auditing anf guidance, you should check out the Security Tools Community Edition page, on Microsoft’s Technet Wiki.
Finally, you might want to follow the Microsoft Security Blog.
Photo Credit: JustEvents via Compfight cc
Installing .NET 3.5 on Windows 8
While installing a third party software on my laptop running Microsoft Windows 8, the operating system informed me that it required to download and install the .NET Framework 3.5. After my consent, it failed to download the package to install. I thought nothing of it and left the task for later.
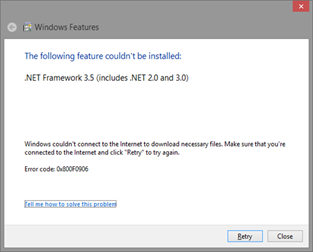
However, this began to be a recurring episode. Even the very .NET Framework setup program would fail. While installing Windows Live Essentials (I really love Live Writer), the error happened again:
The error code 0x800F0906 wasn’t something I knew about and the support link is an awful article which suggest an over the top work around.
So I tried some common sense and analogy. If you’re used to administering Windows 2008 Servers you should know that the Microsoft .NET 3.5 Framework is installed from the feature selection on the add/remove role operation for the Application Server. Windows 7 itself has features that are essential for system administration like Telnet, and yet you have to add them manually.
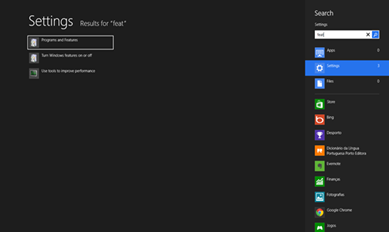
With these aspects in mind I went to the Windows 8 Start screen and typed “Features”. Afterwards I selected “Settings” in the search bar and the desired option appeared, called “Programs and Features”:
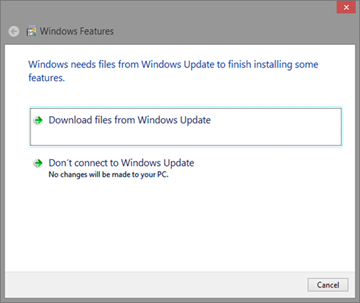
From the list, you just choose the .NET Framework 3.5 and choose to download from Windows Update:
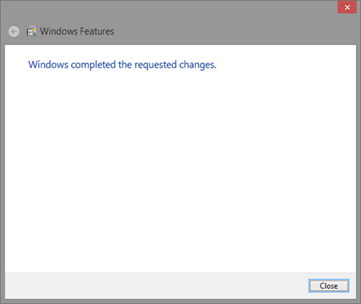
Now just wait for the installation to complete:
I was all set to go. You should be too ![]() .
.
Testing sites for Internet Explorer made easier
Today Microsoft announced a new set of tools to help you support modern and older versions of Internet Explorer.
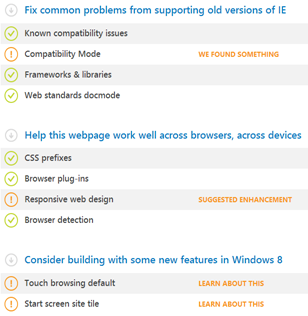
The site makes available a scanning tool that, provided a URL, detects common coding practices that may cause compatibility problems or prevent your users from getting the best possible experience on a webpage rendered on IE. For instance, I ran the scanner on this blog and the report was as follows:
A common problem from supporting old versions of IE was detected. The scanner found that the blog webpage was currently rendering in a Compatibility Mode on Internet Explorer 9 and 10, due to the following tag:
<meta http-equiv="x-ua-compatible"
content="ie=emulateie7">Other “nice to have” issues were detected like a lack of responsive design and no Windows 8 features like a touch browsing interface or a live tile for the start screen.
After removing the compatibility tag, the common problems were all fixed.
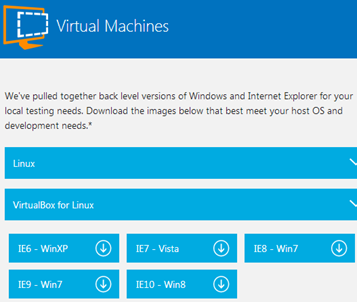
Another interesting part of this site is that virtual machines are made available for both Mac and Linux developers to download and be able to test their Web applications on Internet Explorer, using various versions of the windows operating system and the browser:
Finally I leave you with the insights from two IT professionals about how challenging it is to develop web application given the number of browser and client devices that exist:
Modern IE Homepage: http://www.modern.ie/
No comments :
Post a Comment